1 Oracle Audit
Vault Server Installation Overview
Oracle Audit Vault is a powerful software which can help enterprise consolidate their audit operations to a single source of truth.
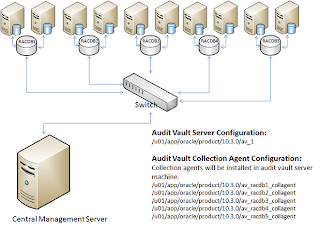

2 Oracle Audit Vault Preinstallation Requirements
This chapter describes the
tasks that you must complete before you start Oracle Universal Installer to
install Oracle Audit Vault Server Release 10.3. It includes information about
the following tasks:
2.1 Logging In to the System as root
$ su - root
password:
#
2.2 Checking the Hardware Requirements
The following are the
memory requirements for installing Oracle Audit Vault Server Release 10.3,
which installs a customized, specially configured release of Oracle Database 11g Release
2 (11.2.0.3):
Minimum: 1 GB of RAM
Recommended: 2 GB of RAM or more
· To determine the RAM size,
enter the following command:
bash-3.2$ /usr/sbin/prtconf | grep "Memory
size"
Memory size: 32256 Megabytes
bash-3.2$
2.2.2 System Architecture
To determine if the
system architecture can run the software, enter the following command:
# /bin/isainfo -kv
This command displays the processor type. The following is the expected output of this command:
Oracle Solaris on SPARC (64-Bit):
64-bit sparcv9 kernel modules
Verify that the processor architecture matches the Oracle software release that you want to install. If you do not see the expected output, then you cannot install the software on this system.
2.2.3 Disk Space Requirements
Disk space requirements
for Installing Oracle Audit Vault 10.3 is listed in below table:
Installation
Type
|
Requirement
for Software Files (GB)
|
Oracle Audit
Vault Server
|
4.45
|
Installation
Type
|
Disk Space
for Data Files (GB)
|
Oracle Audit
Vault Server
|
2.30
|
Amount of free
disk space in the system can be seen using commands below:
# df -h
# df -k
2.2.4 Display Requirements
The minimum resolution for Oracle Audit Vault Server is 1024 x
768 or higher.
2.2.5 Run Level Requirement
Ensure that the system is started with run level 3.
2.3 Checking the Software Requirements
Depending on the products that you intend to install, verify
that the following software is installed on your system:
2.3.1 Operating System
Requirements
Oracle Solaris 10 U6 (5.10-2008.10) or later is required for
Oracle Audit Vault Server Release 10.3.
To determine the distribution and version of Oracle Solaris
installed, enter the following command:
# uname -r
5.10
In this example, the version shown is Oracle Solaris 10 (5.10).
If necessary, see your operating system documentation for information about
upgrading the operating system.
To determine the update level of Oracle Solaris installed, enter
the following command:
$ cat /etc/release
2.3.2 Package Requirements
The following packages (or later versions) are required for
Oracle Audit Vault Server Release 10.3 for Oracle Solaris:
· SUNWarc
· SUNWbtool
· SUNWhea
· SUNWlibC
· SUNWlibm
· SUNWlibms
· SUNWsprot
· SUNWtoo
· SUNWi1of
· SUNWi1cs (ISO8859-1)
· SUNWi15cs (ISO8859-15)
· SUNWxwfnt
· SUNWcsl
To determine if the required packages are installed, enter
commands similar to the following:
# pkginfo -i SUNWarc SUNWbtool SUNWhea SUNWlibC SUNWlibms SUNWsprot \
SUNWtoo SUNWi1of SUNWi1cs SUNWi15cs SUNWxwfnt
If a package is not installed, then install it. See your operating system or software documentation for information about installing packages.
2.3.3 Patch Requirements
The following, or later, patches are required for Oracle Audit
Vault Server Release 10.3 for Oracle
Solaris on SPARC (64-Bit):
Solaris
on SPARC (64-Bit):
Installation Type or Product
|
Requirement
|
All Installations
|
Patches for Oracle Solaris 10:
· 120753-06: SunOS 5.10:
Microtasking libraries (libmtsk) patch
· 139574-03: SunOS 5.10
· 141444-09
· 141414-02
|
Database Smart Flash Cache
|
The following patches are
required:
· 125555-03
· 140796-01
· 140899-01
· 141016-01
· 139555-08
· 141414-10
· 141736-05
|
# /usr/sbin/patchadd -p | grep patch_number(without version number)
For example, to determine if any version of the 119963 patch is installed, use the following command:
# /usr/sbin/patchadd -p | grep 119963
If an operating system patch is not installed, then ask your operating system engineer to install the patch.
2.3.4 Additional Software Requirements
Make sure java 1.6 is installed in your system. Use command
below to identify the version of java installed in your system.
bash-3.2$ java -version
java version "1.6.0_31"
Java(TM) SE Runtime Environment (build 1.6.0_31-b04)
Java HotSpot(TM) Server VM (build 20.6-b01, mixed mode)
bash-3.2$
2.5 Verifying UDP and TCP Kernel Parameters
Use NDD to ensure that
the kernel TCP/IP ephemeral port range is broad enough to provide enough
ephemeral ports for the anticipated server workload. Ensure that the lower
range is set to at least 9000 or higher, to avoid Well Known ports, and to
avoid ports in the Registered Ports range commonly used by Oracle and other
server ports. Set the port range high enough to avoid reserved ports for any
applications you may intend to use. If the lower value of the range you have is
greater than 9000, and the range is large enough for your anticipated workload,
then you can ignore OUI warnings regarding the ephemeral port range.
Use the following command to check your current range for
ephemerial ports:
# /usr/sbin/ndd /dev/tcp tcp_smallest_anon_port tcp_largest_anon_port
32768
65535
In the preceding example,
tcp_smallest_anon_port is set to the default range (32768-65535).
If necessary for your anticipated workload or number of servers
, update the UDP and TCP ephemeral port range to a broader range. For example:
# /usr/sbin/ndd -set /dev/tcp tcp_smallest_anon_port 9000
# /usr/sbin/ndd -set /dev/tcp tcp_largest_anon_port 65500
# /usr/sbin/ndd -set /dev/udp udp_smallest_anon_port 9000
# /usr/sbin/ndd -set /dev/udp udp_largest_anon_port 65500
Oracle recommends that you make these settings permanent. Refer
to your system administration documentation for information about how to
automate this ephemeral port range alteration on system restarts.
In order to make changes permanent edit the file /lib/svc/method/net-init
using file editors like vi and add following lines:
ndd -set /dev/tcp tcp_smallest_anon_port 9000
ndd -set /dev/tcp tcp_largest_anon_port 65500
ndd -set /dev/udp udp_smallest_anon_port 9000
ndd -set /dev/udp udp_largest_anon_port 65500
Always backup the original file before making any changes.
2.6 Checking the Network Setup
Typically, the computer
on which you want to install Oracle Audit Vault Server is connected to the
network. The computer has local storage to store the Oracle Audit Vault Server
installation. It also contains a display monitor and DVD drive. This section
describes how to install Oracle Audit Vault Server on computers that do not
meet the typical scenario. It describes the following cases:
· Installing on DHCP Computers
· Installing on Multihomed
Computers
· Installing on Computers with
Multiple Aliases
2.6.1 Installing on DHCP Computers
Do not install Oracle Audit Vault Server in an environment where
the IP addresses of the Audit Vault Server or the Oracle Audit Vault collection
agent can change. If your environment uses DHCP, ensure that all Oracle Audit
Vault systems use static IP addresses.
2.6.2 Installing on Multihomed Computers
You can install Oracle
Audit Vault Server on a multihomed computer. A multihomed computer is
associated with multiple
IP addresses. This is typically achieved by having multiple network cards on
the computer. Each IP address is associated with a host name. In addition, you
can set up aliases for the host name. By default, Oracle Universal Installer
uses the
ORACLE_HOSTNAME environment variable setting to find the host name. If ORACLE_HOSTNAME is not set and you are installing on a computer that has multiple
network cards, then Oracle Universal Installer determines the host name from
the /etc/hosts file.
Clients must be able to
access the computer either by using this host name or by using aliases for this
host name. To verify this, ping the host name from the client computers using
the short name (host name only) and the full name (host name and domain name).
Both tests must be successful.
Use the following
procedure to set the
ORACLE_HOSTNAME environment variable. For example, if the fully qualified host
name is somehost.us.example.com, then enter one of the
following commands:
In Bourne, Bash, or Korn shell:
$ ORACLE_HOSTNAME=mgtav.mydomain.com.np
$ export ORACLE_HOSTNAME
In C shell:
% setenv ORACLE_HOSTNAME mgtav.mydomain.com.np
The ORACLE_HOSTNAME variable is used to create enterprise
manager url at the end of the installation.
Entries of my /etc/hosts file:
#
#
Internet host table
#
::1
localhost
127.0.0.1
localhost
100.100.100.102
mgtav mgtav.
mgtav.mydomain.com.np loghost
2.6.3 Installing on Computers
with Multiple Aliases
A computer
with multiple aliases is registered with the naming service under a single IP
address but with multiple aliases. The naming service resolves any of those
aliases to the same computer. Before installing Oracle Audit Vault Server on
such a computer, set the
ORACLE_HOSTNAME environment variable to the computer whose host name you want to
use.
2.7 Creating
Required Operating System Groups and Users
Log in to your system as the
root user before you attempt to create these operating system groups
and users.
If you are installing Oracle Audit Vault Server, it requires the
following operating system groups and user:
· The OSDBA group (
dba)
You must
create this group the first time you install Oracle Audit Vault software on the
system. It identifies operating system user accounts that have database administrative
privileges (the
SYSDBA privilege). The default name for this group is dba.
· The OSOPER group (
oper)
This is an
optional group. Create this group if you want a separate group of operating
system users to have a limited set of administrative privileges (the
SYSOPER privilege). By default,
members of the OSDBA group also have the SYSOPER privilege.
The following operating system group and user are required for
all installations:
· The Oracle Inventory group (
oinstall)
You must create this
group the first time you install Oracle software on the system. The usual name
chosen for this group is
oinstall. This group owns the
Oracle inventory, which is a catalog of all Oracle software installed on the
system.
Use the commands below
to create the groups:
/usr/sbin/groupadd -g 101 dba
/usr/sbin/groupadd -g 102 oper
/usr/sbin/groupadd -g 100 oinstall
2.7.1 Creating the Oracle Software Owner User
To
create use enter the following command:
/usr/sbin/useradd -u 100 -g oinstall -G dba,oper -d /home/oracle -m oracle
To
change the password enter the following command:
passwd oracle
2.7.2 Profile of oracle user for Audit Vault Server Home
Below is the contents of .profile file of oracle user for Audit Vault Server Home.
# This is the default standard profile provided to a user.# They are expected to edit it to meet their own needs.MAIL=/usr/mail/${LOGNAME:?}TMP=/tmp; export TMPTMPDIR=$TMP; export TMPDIRORACLE_BASE=/u01/app/oracle; export ORACLE_BASEORACLE_HOME=$ORACLE_BASE/product/10.3.0/av_1; export ORACLE_HOMEORACLE_HOSTNAME=mgtav.mydomain.com.np; export ORACLE_HOSTNAMEORACLE_SID=avdc; export ORACLE_SIDORACLE_TERM=xterm; export ORACLE_TERMPATH=/usr/sbin:/usr/ccs/bin:/usr/ucb:$PATH;export PATHPATH=$ORACLE_HOME/bin:$PATH; export PATHLD_LIBRARY_PATH=$ORACLE_HOME/lib:/lib:/usr/lib:/usr/local/lib; export LD_LIBRARY_PATHCLASSPATH=$ORACLE_HOME/JRE:$ORACLE_HOME/jlib:$ORACLE_HOME/rdbms/jlib; export CLASSPATHexport PATHumask 022ulimit -n 65536#End .profile for audit vault server
2.8 Configuring Kernel
Parameters on Oracle Solaris 10
To create project and add kernel parameters enter the
following commands:
projadd -c "Oracle dba Group for Oracle RDBMS and Audit Vault" group.dba
projmod -s -K "project.max-sem-ids=(priv,4096,deny)" group.dba
projmod -s -K "process.max-sem-nsems=(priv,12000,deny)" group.dba
projmod -s -K "project.max-shm-ids=(priv,4096,deny)" group.dba
projmod -s -K "project.max-shm-memory=(priv,34359738368,deny)" group.dba
projmod -s -K "process.max-file-descriptor=(priv,65536,deny)" group.dba
Verify
the changes using following commands:
cat /etc/projects
Or
projects -l
Add following
lines in /etc/system as root user:
set noexec_user_stack=1
set semsys:seminfo_semmns=1024
set semsys:seminfo_semvmx=32767
set rlim_fd_max=65536
set rlim_fd_cur=65536
set max_nprocs=30000
set maxuprc=16384
2.9 Identifying Required Software Directories
2.9.1 Oracle Base Directory
The Oracle base directory is a top-level
directory for Oracle software installations.
ORACLE_BASE=/u01/app/oracle/
To create the
Oracle Base directory, enter the following commands as the root user:
#mkdir -p /u01/app/oracle
#chown -R oracle:oinstall /u01/app/oracle
#chmod -R 775 /u01/app/oracle
2.9.2 Oracle Inventory
Directory
The Oracle Inventory directory (
oraInventory)
stores an inventory of all software installed on the system. It is required and
shared by all Oracle software installations on a single system. If you have an
existing Oracle Inventory path, then Oracle Universal Installer continues to
use that Oracle Inventory./u01/app/oraInventory/
#mkdir -p /u01/app/oraInventory
#chown -R oracle:oinstall /u01/app/oraInventory
#chmod -R 775 /u01/app/oraInventory
2.9.3 Oracle Home Directory
Oracle Home directory for Audit Vault server is set to the following:
$ORACLE_BASE/product/10.3.0/av_1
To create the
Oracle Audit Vault Home directory, enter the following commands as the root
user:
#mkdir -p /u01/app/oracle/product/10.3.0/av_1
#chown -R oracle:oinstall /u01/app/oracle/product/10.3.0
#chmod -R 775 /u01/
Following
directory is needed to ensure that dbca is able to run after the rdbms
installation.
#mkdir /u01/app/oracle/cfgtoollogs
#chown -R oracle:oinstall /u01/app/oracle/cfgtoollogs
#chmod -R 775 /u01/app/oracle/cfgtoollogs
2.9.4 Staging directory for
Audit Vault Binaries
Download the Audit Vault 10.3 software binaries from
otn.oracle.com and ftp to the location below.
/stage/audit_vault
Unzip the
downloaded files using unzip utility:
unzip server.solaris.sparc64.zip
3 Installing
the Oracle Audit Vault Server
To start the
audit vault server installer go to the directory where audit vault server
binaries are extracted.
cd /stage/audit_vault/server/
./runInstaller
Uncheck the check box if you do not have My Oracle Support account and click on Next button to continue.
Click on Yes to continue because we did not provide My Oracle Support account information.
Select the "Create and configure Oracle Audit Vault" and click on Next button to continue.
Select "Basic Installation" and click on Next button to continue. If you choose "Advanced Installation" you will encounter bug as mentioned in My Oracle Support Document "Advanced Audit Vault 10.3 Installation Fails with: Invalid or missing
Oracle OC4J home [ID 1446663.1]".
Select "Single Instance Audit Vault Installation" and click on Next button to continue.
Provide values for required fields as shown in image below and click on Next button to continue. By default Oracle Audit Vault will create a database with SID=av.
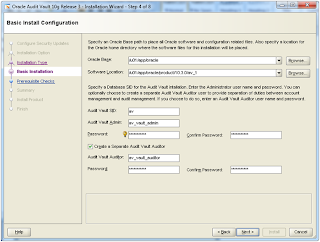
Save the response file if you want to review it later and click on Install button to start the installation.
In a new terminal login as root user and execute the script. The output of the script is shown below.
root@mgtav # id -a
uid=0(root)
gid=0(root)
groups=0(root),1(other),2(bin),3(sys),4(adm),5(uucp),6(mail),7(tty),8(lp),9(nuucp),12(daemon)
root@mgtav #
root@mgtav # /u01/app/oracle/product/10.3.0/av_1/root.sh
Performing
root user operation for Oracle 11g
The
following environment variables are set as:
ORACLE_OWNER= oracle
ORACLE_HOME= /u01/app/oracle/product/10.3.0/av_1
Enter
the full pathname of the local bin directory: [/usr/local/bin]:
The
contents of "dbhome" have not changed. No need to overwrite.
The
contents of "oraenv" have not changed. No need to overwrite.
The
contents of "coraenv" have not changed. No need to overwrite.
Entries
will be added to the /var/opt/oracle/oratab file as needed by
Database
Configuration Assistant when a database is created
Finished
running generic part of root script.
Now
product-specific root actions will be performed.
Finished
product-specific root actions.
root@mgtav #
After the script is executed, click on Ok button. At the end of the installation you will see a window with the urls of the Enterprise Manager configured for Database and Audit Vault. Save these urls for later use.
Save the url at
the end of the Installation:
Hope this helps
Save the url at
the end of the Installation:
Enterprise
Manager Database Control URL - (av) :
https://mgtav.mydomain.com.np:1158/em
Audit
Vault 10.3.0.0.0 URL:
https://mgtav.mydomain.com.np:1158/av
Hope this helps








No comments:
Post a Comment